For some organisations, encryption of data at rest is considered an important security control, especially in the context of cloud solutions. With core Office 365 services (SharePoint Online and Exchange Online) you have the option of controlling your own keys through the method known as Customer Key. But is there anything built-in that provides encryption of data at rest without you having to concern yourself with the intricacies of key management? The answer is ‘yes’ for SharePoint Online – and ‘partly’ for Exchange Online.
SharePoint Online already has service encryption in place with Microsoft-managed keys. For some time Microsoft has had a roadmap item for something similar for Exchange Online. And now (so it seems) the feature is being rolled out. The roll-out itself is not well publicised and I haven’t found any documentation to indicate definitively how you can determine whether it has hit your Exchange Online tenant. That said, there is a clue available through the Get-MailboxStatistics cmdlet (see example below).
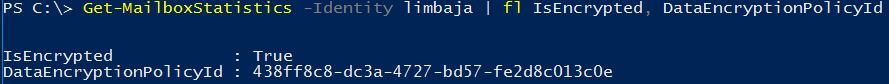
What this indicates to me is this mailbox in my tenant is encrypted. I have created no data encryption policies for Exchange Online, so this must be one that Microsoft manages. This is further verified by running the Get-DataEncryptionPolicy cmdlet (see example below).

As you can see, the cmdlet returns no results, which means the data encryption policy applied to my mailboxes is not one I have any control over. In fact I’m not even able to see any of the properties associated with the policy.
Having looked at a couple of different tenants, it seems the policy is already reasonably widely deployed. The DataEncryptionPolicyId with a value of 438ff8c8-dc3a-4727-bd57-fe2d8c013c0e appears to be common to all the tenants I have viewed.
While it would be nice to have more detailed information about the Exchange Online service encryption roll-out, it is at least encouraging that Microsoft is taking data at rest seriously and improving the the security of the service in this way.

Are you on E5, maybe that is why you see your mailbox as encrypted?
How do you know that they are rolling it out for all customers? For example I am on E3 and i dont see my mailbox as encrypted.