I fell foul of this one the other day and it took a while to figure out what to do about it. Here’s the scenario:
You deploy a new Group Policy Preferences (GPP) setting to create a folder on a workstation and specify the “Apply once and do not reapply” option. Unsurprisingly, this implies the GPP item will apply only once and will not run again!
But what if you have a problem on a specific target computer where the computer thinks it has already applied the GPP setting once? You won’t get the setting to reapply using the traditional gpupdate /force option. Instead you must look in the registry of the affected computer and look for the RunOnce entries. These are located here:
HKEY_CURRENT_USER\Software\Microsoft\Group Policy\Client\RunOnce
HKEY_LOCAL_MACHINE\Software\Microsoft\Group Policy\Client\RunOnce
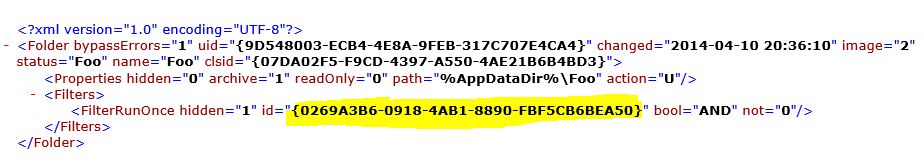
The registry string values (REG_SZ) shown correspond to the RunOnce settings. Instead of descriptive text these entries have (spectacularly unhelpful) GUID-style names.
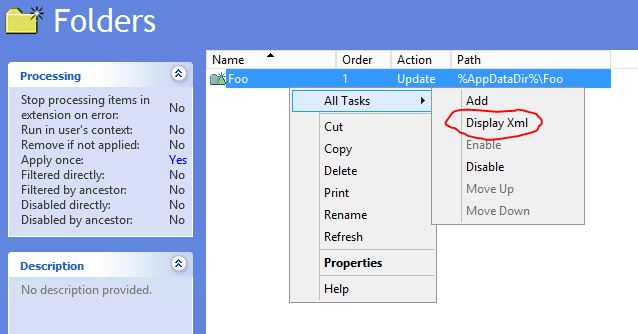
Ok, so armed with this information, how do you go about identifying the GUID-style name with your GPP setting? Don’t be led down the path of thinking the GUID-style name will match the GUID of your GPO – it doesn’t. That kind of make sense as a single GPO can have multiple GPP settings. The answer lies buried within the XML of the GPP setting. To get to the XML, right-click the GPP item within the GPO Editor and select All Tasks -> Display XML. Once you can see the XML look for the line starting with “FilterRunOnce” line. The value shown next to the “ID” is the one that corresponds to the registry entry.
To get the GPP setting to re-apply to the problem workstation, simply delete the relevant string value from the registry and force the policy to re-apply (gpupdate /force).



Nice research!
This was exactly the information I was looking for, thanks for this!
Hello from 2022.
Thanks for the info, exactly what I was looking for! 🙂