Here’s something I discovered recently and would like to share with you. If you are using Skype for Business Online and want to control access to it using Conditional Access policy, you should be aware that under certain circumstances the control can be completely bypassed.
The problem has to do with the fact that Conditional Access only kicks-in when the authentication attempt is from the following:
-A web browser
-A client app that uses modern authentication
-Exchange ActiveSync
Conditional Access is not processed by legacy clients, i.e. those that do not support modern authentication. For example, the Skype for Business 2015 client (the one that ships with Office 2013, and without modern authentication enabled) cannot interpret the Conditional Access policy and as such will bypass the controls.
Let’s look at this in more detail.
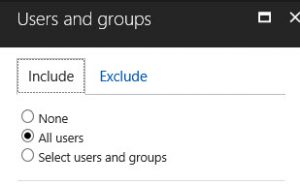
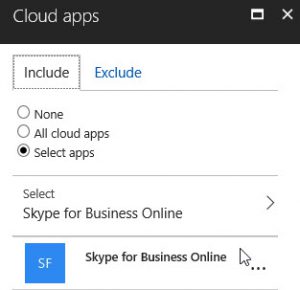
In this example, I have created a new Conditional Access policy specifically for Skype for Business Online.
I want all users to be included in the policy.
I only want the policy to apply to Skype for Business Online.
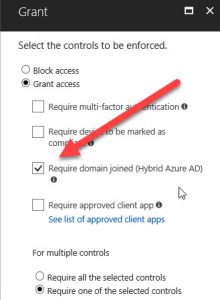
And finally, I only want access to be permitted from Hybrid Azure AD devices (i.e. those that are joined to on-premises AD and device registered in AAD).
I’ve left all of the other settings within the policy at their defaults. Once I’ve enabled and saved the policy the next thing to do is test whether it works as expected.
The first test is to determine whether the policy blocks access from the Skype for Business 2016 client (click-to-run version) running on a device that does not meet the Hybrid Azure AD condition. As expected, the access is denied along with a friendly and reasonably helpful error message (shown below).
The second test is run from a machine that also doesn’t meet the Hybrid Azure AD condition, but this time the sign-in attempt is from the Skype for Business 2015 client. In this test, the user is able to sign-in without any problems.
The Skype for Business 2015 client is effectively able to completely bypass the Conditional Access control, thereby rendering it effectively useless. Your Skype for Business Online instance can be accessed from any device from anyone who has valid credentials. The question is then what you can do about it? There’s currently no silver bullet to handle this scenario. Microsoft makes provision to block legacy client apps for SharePoint Online and, to an extent Exchange Online, but there is nothing obviously available for Skype for Business Online.
One workaround is to force MFA (at the Azure AD level) for the users that need to access Skype for Business. With MFA enabled the user sees the following (spectacularly unhelpful) error when trying to sign-in from the Skype for Business 2015 client.
I understand that Microsoft are (as of November 2017) looking a method – currently in private preview – to address issues with legacy clients and Conditional Access, not just for Skype for Business, but across the board. Watch this space.




ADFS + Claims rules are the way to go for now, but MS has been making some really good progress in the CA and mobility space so looking forward to a more straightforward solution through AAD.