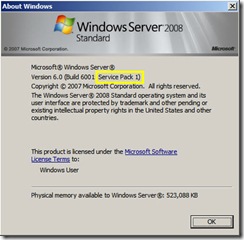
If you’ve managed to get some hands-on experience with the RTM Windows Server 2008, you might be surprised to see the version shown as Service Pack 1. Relax, you haven’t been in a coma – this really is what the RTM release calls itself (see below).
The reason for Service Pack 1 moniker is so that service packs and patches for Vista and Windows Server 2008 can be streamed together. From a customer perspective this is potentially less confusing than was the case with, say, Windows XP and Windows Server 2003 where the service packs were not aligned.
The cynical among us might also consider than many organisations hold off from deploying a new Microsoft release until at least SP1. In other words, this is perhaps a clever ploy from Microsoft to push customers towards early adoption.
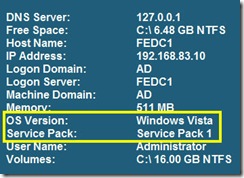
One interesting facet of the close alignment between the Vista and Windows Server 2008 is that it appears to have caused some confusion with BgInfo, as shown in the screenshot below from a Windows Server 2008 machine.

I know a few companies now are running and selling dedicated windows 2008 servers. Server Intellect even has a fully managed solutions which we run. It is a good core OS and will get strong over time like all the other pryor OS’s I mean look at XP it is now a very stable OS.